
Cybersecurity Tips: Leveraging At-Home Technology Safely
Affiance Financial is pleased to share the following article by FRSecure. FRSecure is a business-to-business cybersecurity service provider based out of Minnetonka. More information about the company can be found at FRSecure.com.
Whether it’s socially, work-related, financially, or otherwise, our drastic increase in time spent at home has entirely altered the way we utilize technology. Most of us are using new programs, apps, and devices to do what we’d traditionally do face-to-face. And even as things begin to open up, it is likely that many of these new technologies will remain a part of our lives. This change in the way we conduct our daily lives has certainly affected a lot. Whether we realize it or not, cybersecurity sits near the top of that list.
As we alter the way we utilize the technology available to us or add new technologies to our repertoire, the risk of data compromise goes up and our privacy goes down. But, with a little effort and an understanding of the technology we utilize, we can continue to use technology to our advantage.
Popular Remote Tech and How to Use it Safely
Outside of work, we’ve adapted to using tons of platforms to keep us connected safely. Again, any time we use platforms connected to the internet, we risk our information being misappropriated, but there are things we can focus on to avoid compromise and minimize the impact if something were to happen.
Zoom (and Similar Videoconferencing)
Videoconferencing might be the type of technology that blossomed the quickest with the pandemic. With people required to stay at home, businesses, families, and friends needed to find creative ways to stay in touch. Whether it’s a Zoom meeting with your financial advisor, or a virtual game night with friends, videoconferencing services have provided us an incredible platform to connect.
Security and Privacy
Zoom particularly has gotten recent flak for its lack of seriousness in the privacy and security department, but they’ve had impressive responses to the feedback, and it’s important to note that the risk of using these platforms is already minimal. We use the platform ourselves at our office for both internal and external meetings.
Things like “Zoombombing” (unwanted people unexpectedly dropping into meetings), malware (virus) injections, and the sharing/leaking of personal data and photos have all seemingly been fixed on Zoom’s end.
Generally speaking, Zoom is quite safe to use, and there are some things you can do within the platform to make it even safer.
Using it Safely
Here are security measures we recommend you employ when using Zoom for office and personal use:
- Set screen sharing to “Host-Only” to prohibit undesired participant sharing.
- Disable “Join Before Host” so participants can’t enter the meeting early. Without this turned off, it’s possible for attendees to utilize chat, video, and file sharing without monitoring.
- Disable private chat to avoid participant-to-participant communication.
- Disable “File Transfer” so that if an unwanted visitor does join, they can’t share anything malicious.
- Disable “Allow Removed Participants to Rejoin” so removed attendees can’t slip back in.
- Enable “Mute Participants on Entry” to minimize distracting background noise and to avoid something unwanted being said accidentally.
- Enable "Only Authenticated Users Can Join Meetings," which will force users to sign into Zoom to participate.
- Add a “Co-Host” if you are working with someone who can help moderate.
- Utilize the “Waiting Room” feature (activated by default) to control attendees.
- Set meeting passwords and make them as complex as possible.
- Be aware of what’s in the background of your video. Don’t allow your webcam to catch any sensitive information.
- Close all unnecessary windows before screen sharing to avoid accidentally showing sensitive emails or information.
- Only record meetings if absolutely necessary. Be mindful of the information in the recording and who you share it with.
- Do not make your meeting links publicly available. This increases the chances that someone unwanted can join.
- Do not post screenshots of your meeting on social media. This may lead to the oversharing of personal information.
- Always report any suspicious activity to your work security team and/or Zoom.
Virtual Games
Few things in life are as good as opening a bottle of wine, grabbing some snacks, and playing games with friends and family. We’re quickly reminded of how much we miss simple things like this now that we can’t do them as readily. Forgetting security for a second, we're quite lucky we live in the interconnected time that we do during this pandemic, or it would have been downright impossible to see the people we care about at all.
Hosting a virtual game night is something that a lot of people have used as a way to stay connected and keep some semblance of normalcy.
Security and Privacy
Most internet-connected platforms account for security and privacy as they go through the development process. Because of this, online gaming platforms will be relatively safe to use.
The biggest concern with most of these applications is who they share your information with—apps they integrate with, advertisers they send user information to, etc.
Using Them Safely
Going back to this idea of risk, there’s a risk in doing anything online, so it’s important to understand what level of risk is acceptable for you. So, even though there are measures put in place to keep you secure by the developers, the onus is on you to vet these platforms and decide what’s acceptable to you before using them.
- Read the privacy policy – Yes, those long and boring privacy policies that everyone pretends to read are important. Use them to understand how the platform intends to use your information. Will they sell it? Can you request they remove your data, or can you download your data from them to see what they are collecting? Ensure you’re okay with how they treat your data before creating an account or downloading the platform.
- Research the security of the program – If the site has a known vulnerability or compromise, you should look elsewhere. Some sites will tell you if a platform has a known breach. HaveIBeenPwned is a favorite of ours.
- Download or access direct – Don’t download programs from third-party sites, and don’t sign into accounts from other platforms (particularly email). It’s fairly easy to spoof download and login pages to gain credentials or send malicious files. Going directly to the program’s site is the easiest way to avoid this type of attack.
- Check reviews and download numbers – There’s safety in numbers. If an application or program has good reviews and a high number of downloads, people have had good experiences with it. An easy way to spot shady apps is by bad ratings and small download numbers. Steer clear of those.
Some Apps We Suggest
Fairly recently, we put together a list of some of the more fun technologies, platforms, and sites you could use for your virtual game night. The whole post can be found here, but here are some highlights:
Games:
- Remote Yahtzee – https://www.memory-improvement-tips.com/support-files/yahtzee-score-sheets.pdf
- Houseparty - https://houseparty.com/
- Online Bingo - https://letsplaybingo.io/
- Jackbox Games - https://www.jackboxgames.com/
Virtual Connect:
- Zoom - https://zoom.us/
- Wire - https://wire.com/en/
- Skype - https://www.skype.com/en/get-skype/
- Google Hangouts - https://hangouts.google.com/
- FaceTime - https://support.apple.com/en-us/HT204380
Telehealth Platforms Like Virtuwell
Especially given the COVID-19 pandemic, telemedicine has become an incredibly useful tool in receiving certain medical diagnoses from the comfort of home. With the rapid rate of spread of COVID-19, for a trivial concern it’s typically much safer to consult with a doctor online than to be seen in a setting surrounded by other sick people—and it helps lessen the demand for on-site medical professionals.
Security and Privacy
Thankfully, the healthcare industry has been long known as one of the most regulated in terms of information security and data privacy. The Health Insurance Portability and Accountability Act, better known as HIPAA, was introduced in 1996 and outlines measures healthcare professionals must take to protect Protected Health Information (PHI). Telehealth falls under the same requirements.
And, the HHS Office for Civil Rights (OCR) has provided additional guidance to remind healthcare companies of the expectations during this pandemic. Still, there are concerns including the increased bandwidth needed for accommodating the number of people opting for telehealth during the pandemic and the risks associated with telehealth workers handling sensitive information while working from home.
Using it Safely
Many providers have an internet-based portal where you can input your medical information, insurance information, images of your health concern, copay methods, etc. Since the online portal asks you for this information in advance, you should never have to share it again via email or phone. If this is something that’s being asked of you from an inbound email or call, place an outbound call to the number directly on the website to your telehealth provider and inquire about the request. Since you called them, you know for a fact you’re only providing this information to your provider and not a scam caller.
Additionally, many of the health concerns will require photographs for diagnosis. Simply be aware of what’s in those photos. Any sensitive information should be left out, and you should always be mindful of what’s in your background. It’s easy to have sensitive information or location giveaways in the background if you’re not careful.
Best Practices for Remote Work
Working remotely poses unique security challenges for businesses and their employees. Simply put, it’s harder for employers to monitor workers who are not on-site, and it’s easier for employees to fall into a trap of being lax given the comfort of being home.
But unfortunately, malicious access under your account will make you suspect number one, and it’s important to follow proper office policies, procedures, and guidelines to avoid any potential negative consequences.
You can avoid this by using technology and smart practices to your advantage.
Things to Consider for Work Devices
Whether it’s a laptop, desktop computer, or a personal device you use to remote desktop into work, we must treat our devices the same as we would in the office.
Lock Up
Any time you leave your device, make sure that you lock it. We trust our significant others not to do something they shouldn’t. But kids who don’t know better are home and cats walk across keyboards—weirder things have happened. This is one of the easiest ways to avoid something bad happening, and it’s a good habit to get into for when you return to the office as well.
Windows key + L will lock your screen on a Windows PC, and Command + Control + Q will lock your screen on a Mac.
Watch What You Do
If you wouldn’t download a particular program or visit a particular site at the office, you also shouldn’t do it at home. There’s risk in logging into any site and downloading any program, so play it safe by separating your work and personal activities.
If you’re using a personal device to virtually access your work desktop, be extra mindful of what you’re doing on and off your virtual machine.
Patch Everything
You know those annoying little notifications that pop up telling us we need to do an update? They seem inconvenient, but they’re critically important. Developers make constant improvements to their programs as new information becomes available. Many times, app and program updates account for a recently discovered security gap (this is sometimes referred to as patching). If you ignore these updates, you may not be protected against the vulnerabilities that exist in the older versions.
Run Antivirus and Antimalware
A work laptop or desktop device is likely equipped with this before you even receive it, but if you’re expected to use a personal device to connect to a work device remotely, you may not. Ensure your device has antivirus and antimalware programs installed and ensure both are always up to date.
Turn on Your Firewall
Most operating systems have firewalls built into their settings. Effectively, these act as a gate between your computer and the bad things that exist on the internet. Especially if you’re using a personal device to work, make sure this is turned on in your system settings.
General Network Practices
Change Default Router Settings
Wireless routers often come with default usernames and passwords. Because of this, attackers who get ahold of these default passwords will try them on as many routers as they can. If you don’t change your router password and network name to something unique, your risk of compromise increases.
Use Good Passwords
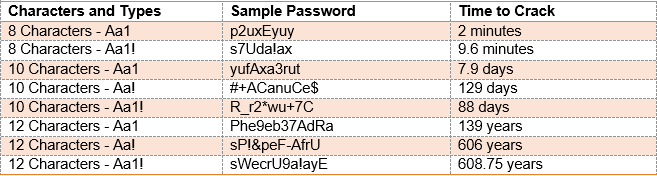
Good passwords and passphrases are paramount to good security. Affectionately called “long and strong,” we recommend all passwords be at least 8 characters long and include some mixture of lowercase letters, uppercase letters, numbers, and symbols. You can double down by making sure common substitutions like “0” for “O” are not used.
Here are some examples of passwords and how long they’d take to crack using a common hacking technique and program:
Create a Guest Wi-Fi Network
Almost all routers will allow you to create multiple networks within the same Wi-Fi. Not that you’re having tons of guests over at the moment, but using a guest network allows you to control what is happening on the main network. This is especially important when connecting work devices. If your guest network is compromised, the network your work device is connected is more likely to remain intact.
Create a Separate Network for IoT Devices
IoT, or Internet of Things, is a fancy way of saying devices that connect to the internet. As devices such as Amazon Echo, Google Home, Roombas, and even smart refrigerators (yes, that’s a thing) become more prevalent, so does the concern for security. Just as mentioned with guest networks, separate the connection of your IoT devices from your other ones—especially work computers.
VPN if You Can
VPNs are programs that allow you to connect to your home internet connection from your work devices, but it will hide or change where the information is being sent from and to. This creates a secure and encrypted connection that will help protect information.
When using a work computer on a non-work network like your home wireless, a coffee shop, airport, etc., connect to the network through a VPN if possible.
Other Things to Think About
Use Password Managers
Simple passwords are bad. Reusing passwords is bad. Writing your passwords down is bad. But we all have so many accounts these days that it’s impossible to make them strong, different, and private without forgetting them, right? That’s just not true anymore. Password manager programs are great tools for us to be able to generate and store random and long passwords without forgetting them or having to put them on a Post-It on your monitor. You’ll only need to remember your master password, and the program will do the rest. LastPass is one we commonly recommend.
Enable Multifactor Authentication Everywhere Possible
Effectively a confirmation step after logging in, multifactor authentication forces a user to prove their identity with a second step. This is often a text message with a code to the account’s phone number, a code sent to the email address on the account, or a third-party code-generating app like LastPass or Google Authenticator. If someone was able to figure out your password and log in to your account, they'd also need to have access to your phone or email to get in with multifactor turned on. This added level of protection is one of the simplest yet most effective solutions that exists today, and we’d suggest you implement it on any account that it’s an available feature on.
Spotting and Reporting Suspicious Activity
Stay Up to Date
At the end of the day, good security stems from strong education and training. Make yourself aware of some of the common scams that exist in the world today, so you know what to look out for. The Federal Communications Commission (FCC) does a good job of posting the current scams they’re aware of. If you can familiarize yourself with that list, it’ll help you know what to look out for. https://www.fcc.gov/general/frauds-scams-and-alerts-guides
Check Your Emotions
Attackers feed on emotion, targeting with urgency and perceived importance. If you can take the emotion out of it and analyze the request first, it’ll make it much less likely that you fall victim to a scam. The best way to do that is by educating yourself and thinking critically before acting on any requests.
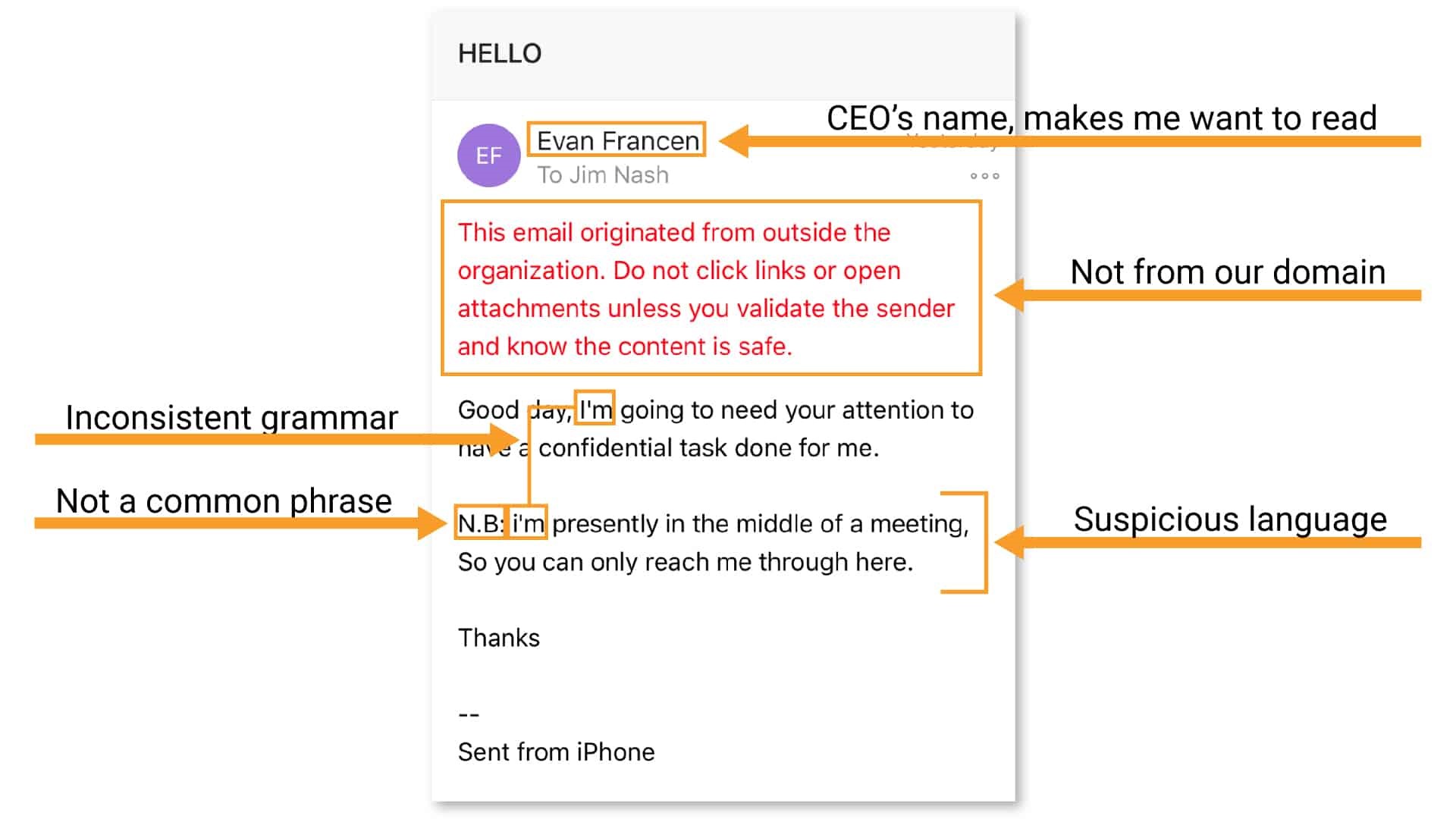
Analyze Emails
There are some pretty quick ways to spot phony emails. A lot of attackers have roots outside of the United States, so bad or strange grammar is often a quick way to spot a fishy email. Misspelled words can often be an indicator as well.
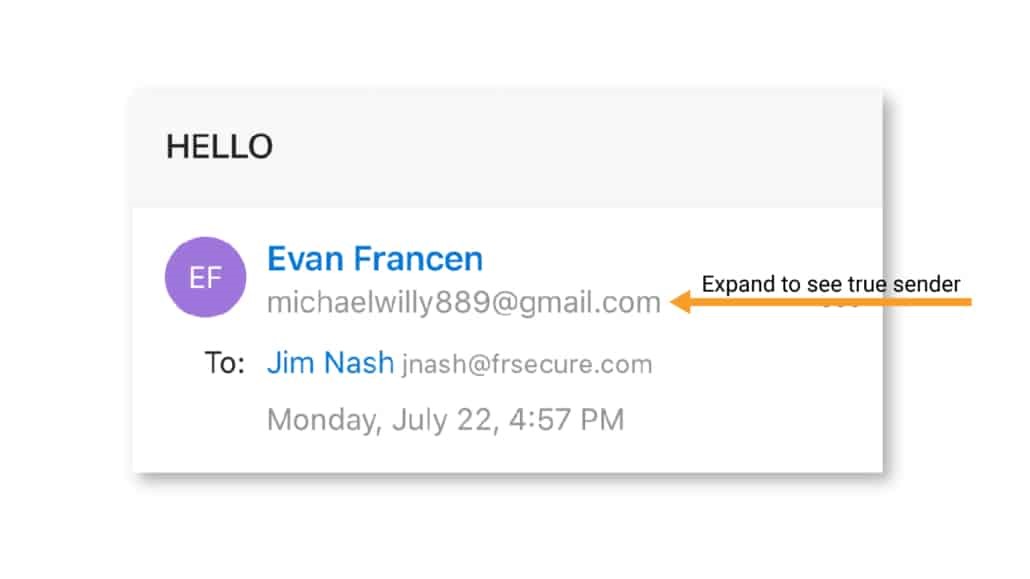
You can double-check by expanding the sender information in the email, or better yet, call the person who “sent” you the email and ask them to confirm that the request came from them.
I mentioned it before too, but don’t log in to an account via email—especially your bank accounts. If it seems like something important, go to the site directly and log in there to look into the request.
Know What You’re Normally Asked
There are certain things that your trusted connections simply won’t ask you over the phone or email. For example, your financial advisor is never going to ask you to send them an important financial document via email. They’d only use a secure file sharing service like ShareFile. If you’re being asked to attach your important financial info via email, it may be a sign of a scam.
Report Anything Suspicious
Whether it’s from your financial advisor, someone at work, a company you’ve purchased something from, etc., it’s important that the group being impersonated is alerted that a scam is out there.
This could be a sign that their email server has been compromised and should be looked into. If nothing else, it alerts them that they may need to take action against the scammers and communicate the scam with their clients.
On a grander scale, you can certainly report any suspicious activity to your email provider (mark as spam), your company’s IT or security team (who may be able to block that sender altogether), and the FCC (if it’s not on their list of known scams already). This will hopefully help limit further attacks against you or others.
Wrapping Up
We have an incredible advantage living in the technical age we do. It allows us to work and stay connected with family and friends from home (and nearly everywhere on the globe). But, as we continue to increase the amount of information that exists online, as well as the number of platforms we utilize, the risk of our information being compromised goes up.
Thankfully, by implementing some programs, technologies, education, and training, we can continue to safely use those technologies to our advantage.
Keep these top-of-mind as you continue to leverage these platforms to stay connected as we socially distance.
This article is being provided for informational purposes only and is believed to be factual and up-to-date. Affiance Financial does not guarantee its accuracy and it should not be regarded as a complete analysis of the subject discussed. All opinions reflect the judgment of the third party author as of the date of the post and are subject to change. Affiance Financial and Private Client Services are not responsible for comments made by third parties.

